A key replacement order is a request that is made in the following cases:
- When changing a physical key to a virtual one
- When a key breaks, to transfer licenses from a broken key
- When transferring the software security code from one key to 2 or more, if several security codes were generated for one key
- When combining software security codes from 2 or more keys to 1 key, if several security codes were generated for 2 or more keys
- When upgrading the software — updating its version to a more functional or modern one.
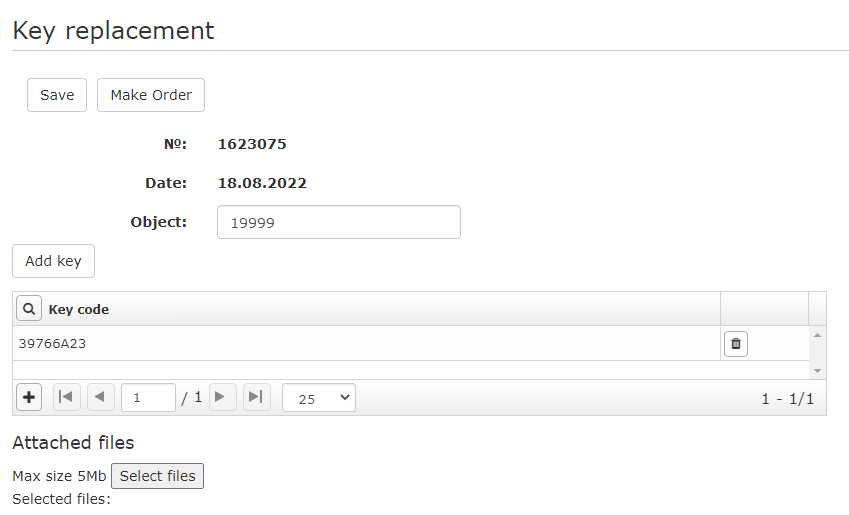
Instructions for automatic confirmation of a request for key replacement
- In the Licensing System, go to Orders and select the Replace Keys Order
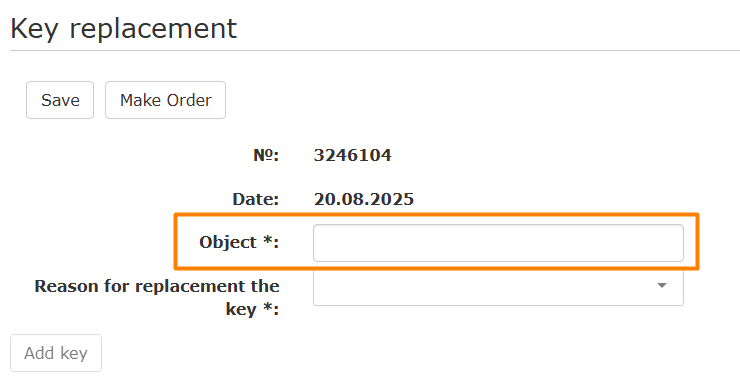
- Select the object for which you need to create an Order
- Fill in the required field Reason for key replacement
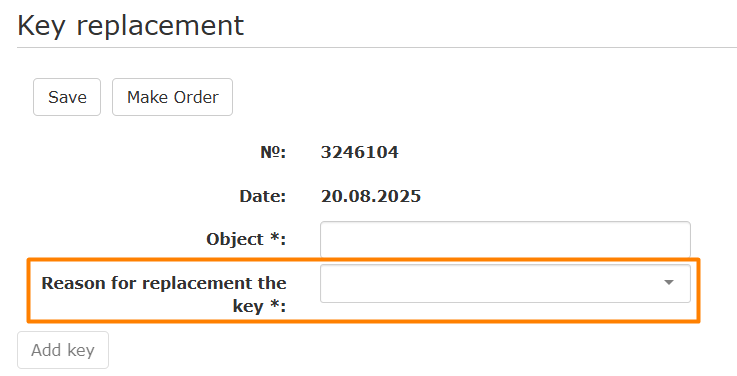
- Please select one of the options for the replacement reason
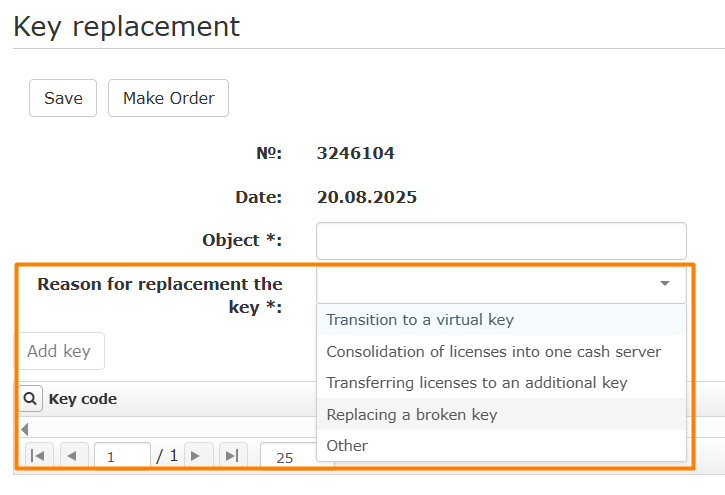
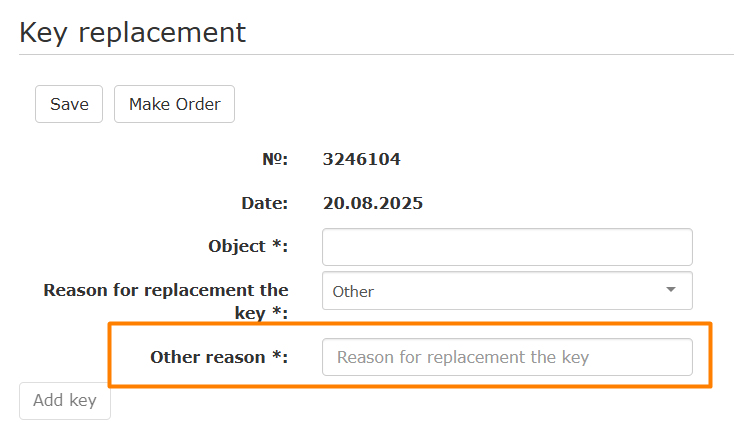
- When you select the Other value, a window appears for entering a comment.
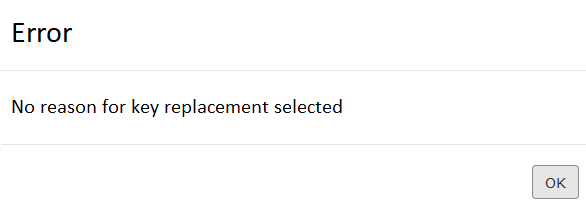
- When trying to order an application, without a filled field, an error is displayed: The reason for replacing the key is not filled
Click the Order button to submit your request.
If you need to replace a physical key, please return it within two months of making a replacement key order.
To return physical keys:
- Collect the keys from the object and make an order for the return of software security keys. Here is an order template
- Send the keys to the r_keeper manager in any convenient way— by mail or by courier. Be sure to attach a cover letter — the original key replacement order
- The r_keeper manager will accept the keys. Within 10 working days, they will check the quantity, authenticity and availability of the software security code linked to the key.
If necessary, the key will be sent to the r_keeper key supplier for authenticity verification. The key verification by the supplier includes verification of the series and key number, which must match the list of numbers.
When using specialized r_keeper software to remove the crypto-algorithm from a physical key, you can be exempted from the key return procedure.
In case of theft or destruction of the key— if there was a fire, flood, earthquake, etc. — provide supporting documents about the incident. Based on these documents, r_keeper will restore the key and the software linked with it at the cost of the key.